Overview
This project demonstrates the use of Infrastructure as Code (IaC) tool HCL Terraform to create all the necessary cloud components to run a web application securely, including networking, databases, load balancers, and container hosting. IaC tools like Terraform, and its open source derivative OpenTofu, enable setting up an entire technology stack with one configuration.
This code is an IaC configuration that sets up a complete web application infrastructure in AWS cloud.
Inputs
- Basic settings like region, project name, and environment
- Network settings (CIDR ranges for VPC and subnets)
- Database configurations (engine type, username, password)
- Domain name and SSL certificate details
- Container image details for the application
Outputs
- The final website URL where the application can be accessed (https://[record_name].[domain_name])
Important Logic Flows
- The code uses Terraform modules (reusable components) for each major piece of infrastructure
- Each module depends on resources created by previous modules (for example, the RDS database needs the VPC and security groups first)
- The networking is structured in layers: public subnets for load balancers, private subnets for application, and separate private subnets for database
- Auto-scaling is configured to automatically adjust resources based on demand
The code achieves this by using Terraform's declarative syntax, where you specify what you want (the desired state) and Terraform creates it in AWS. It's like giving a blueprint to an automated builder who then constructs everything according to the specifications.
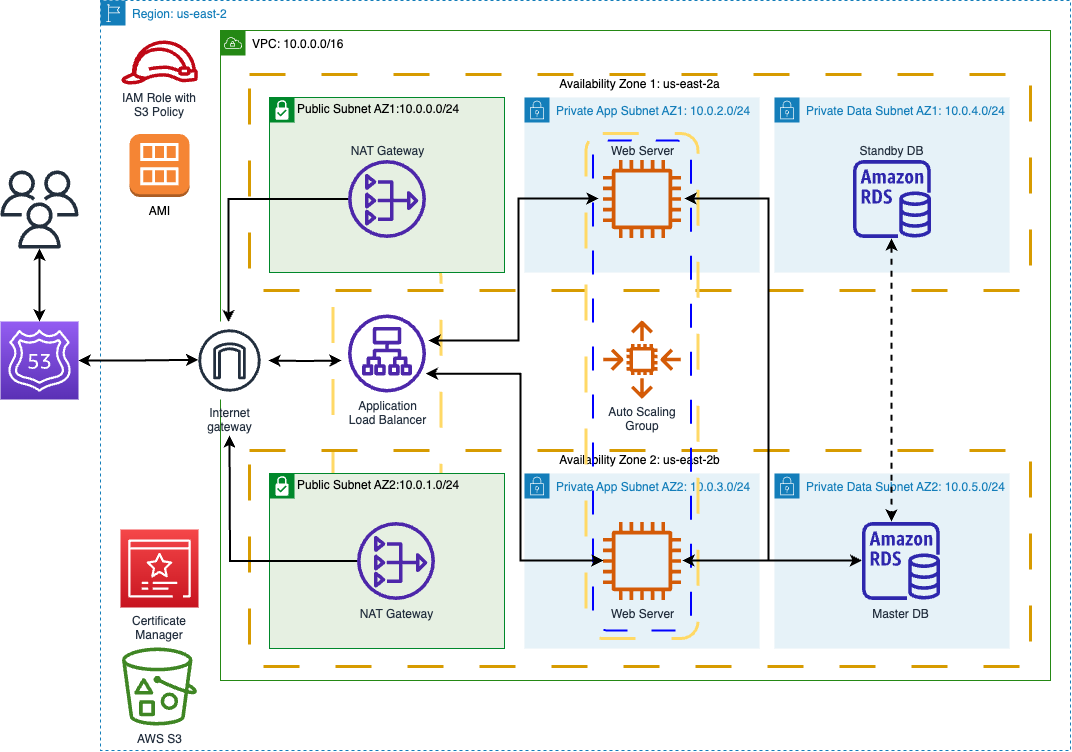
AWS Services deployed
- Three-tier VPC with public and private subnets in 2 availability zones.
- Internet Gateway to allow communication between instances in VPC and the Internet.
- Multiple Availability Zones for high availability and fault tolerance.
- Public Subnets for resources such as Nat Gateway, Bastion Host, and J Application Load Balancer.
- Private Subnets to protect the application and database servers.
- Nat Gateways to allows resources in the private subnets access to the Internet.
- MYSQL RDS for relational database.
- EC2 Instances to host the web application.
- Application Load Balancer to distribute web traffic to EC2 instances in ^ multiple AZs.
- Auto Scaling Group to dynamically launch EC2 instances for highly availability, scalability, fault-tolerant, and elastic.
- Route 53 to register domain name and create record set.
- AWS S3 to store application codes.
- IAM Role to give EC2 permission to download the application code from AWS S3.
- Certificate Manager to encrypt data in transit.
How it works
- Create a Virtual Private Cloud (VPC) with public and private subnets for network isolation
- Sets up NAT Gateways so private resources can access the internet securely
- Creates security groups to control network access between components
- Provisions a database (RDS) in the private subnet
- Sets up SSL certificate for secure HTTPS access
- Creates a load balancer to distribute traffic
- Sets up S3 bucket for storing application configuration
- Creates necessary IAM roles for security
- Create and update Elastic Compute Cloud (EC2) instances and install web application
- Sets up auto-scaling to handle varying loads
- Creates DNS records so users can access the site via a domain name
- MySQL Workbench to import SQL data into the RDS data
Tech Stack
- AWS Account
- AWS CLI
- GitHub account
- GitHub repo with Terraform modules (modules can, optionally, be sourced locally)
- Git
- Terraform
- ECR Repo
- SSH client
- EC2 Key Pair
- dBeaver or MySQL Workbench
IaC Steps
- Create VPC with 2 public and 2 private subnets
- Create NAT Gateway
- Create Security Groups
-
Create RDS instance and empty database and users
- Manually create Bastion host for SSH tunnel to RDS endpoint
- Manually Use SQL client to connect to database to create tables and import seed data. TODO: Created database from snapshot.
- Request Amazon TLS Certificate
- Create Application Load Balancer for public subnets
- Create S3 Bucket for environment file
- Create IAM Assumed Role for ECS Task execution
- Create ECS Cluster, Task Definition, and Service
- Create Auto Scaling Group
- Add DNS record to Route 53