Overview
This web application uses Auth0 for a complete authentication system with secure session management, user authorization capabilities, and role-based access control.
Auth0 uses the OpenID Connect (OIDC) Protocol and OAuth 2.0 Authorization Framework to authenticate users and get their authorization to access protected resources. With Auth0, you can easily support different flows in your own applications and APIs without worrying about OIDC/OAuth 2.0 specifications or other technical aspects of authentication and authorization.
Auth0 Authorization Code Flow
The Authorization Code Flow (defined in OAuth 2.0 RFC 6749, section 4.1), involves exchanging an authorization code for a token.
This flow can only be used for confidential applications (such as Regular Web Applications) because the application's authentication methods are included in the exchange and must be kept secure.
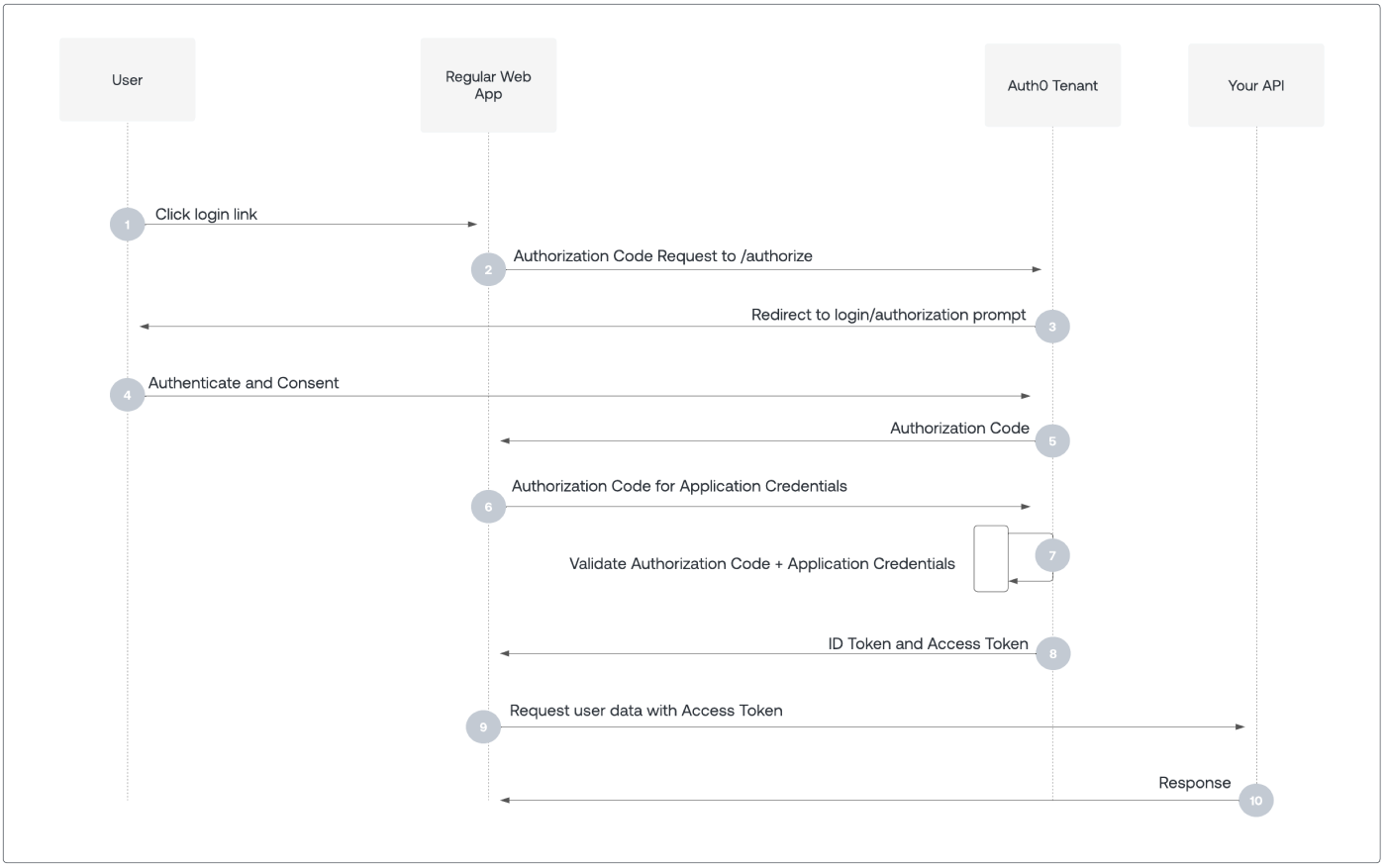
-
User selects Login within application.
-
Auth0's SDK redirects user to Auth0 Authorization Server .
-
Auth0 Authorization Server redirects user to login and authorization prompt.
-
User authenticates using one of the configured login options, and may see a consent prompt listing the permissions Auth0 will give to the application.
-
Auth0 Authorization Server redirects user back to application with single-use authorization code.
-
Auth0's SDK sends authorization code, application's client ID, and application's credentials, such as client secret or Private Key JWT, to Auth0 Authorization Server (
/oauth/tokenendpoint). -
Auth0 Authorization Server verifies authorization code, application's client ID, and application's credentials.
-
Auth0 Authorization Server responds with an ID token and access token (and optionally, a refresh token).
-
Application can use the access token to call an API to access information about the user.
-
API responds with requested data.
Presentation Layer
- Auto0 Universal Login integration
- Login/Signup forms through Auth0 hosted pages
- Session status indicators in navigation
- Protected route UI handling with redirects
Application Layer
-
Authentication flow in
auth/views.py - Session management with Flask sessions
-
Route protection using
@requires_authdecorator - Token lifecycle and expiration handling
Data Layer
-
Auth0 Management API integration via
Auth0Managementclass - User data and role management functions
- Token storage and session persistence
- Auth0 tenant configuration management
Security Features
- OAuth 2.0 compliant authentication flow
- Secure session handling with expiration checks
- Automatic token refresh mechanisms
- Protected route middleware implementation